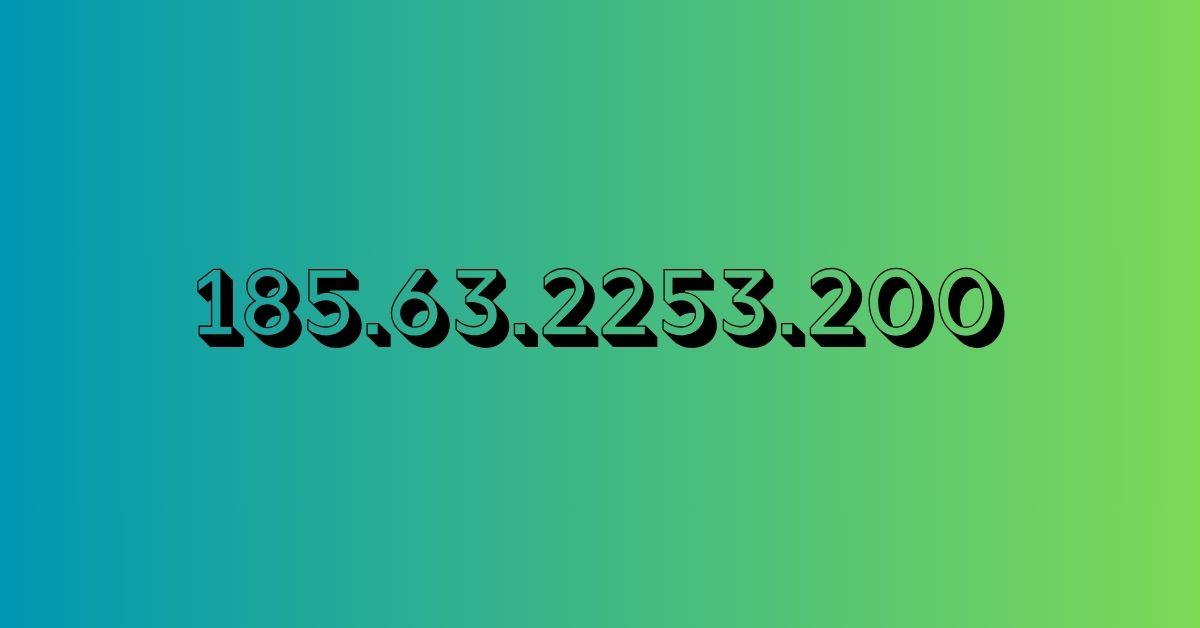In the first 100 words, here’s what you need to know about 185.63.2253.200. It looks like an IPv4 address, but the third segment (“2253”) exceeds the allowable range of 0–255. This invalidation triggers confusion when the string appears in logs, forums, or config files. Understanding why it persists, what risks it poses, and how to validate IPs helps sharpen digital hygiene and cybersecurity awareness.
Why 185.63.2253.200 Isn’t a Valid IPv4 Address
IPv4 addresses follow the format where each octet ranges from 0 to 255. In this case, “2253” far exceeds the upper limit, immediately disqualifying the sequence as a legitimate address. While it mimics an IP structure, it cannot route, ping, or be geographically traced.
How It Shows Up and Why It’s Not Always Harmless
Typographical or Formatting Errors
Often, this string results from a typo—perhaps someone intended “185.63.253.200” or “225.200”.
Placeholder or Test Data
Developers may use invalid address patterns like this when scripting or mocking examples, particularly in educational or demo setups.
Potential Cybersecurity Triggers
In some cases, malformed strings are used in honeypots or evasion tactics. Attackers may spoof invalid IPs to confuse logging or scanning tools.
Cybersecurity Implications of Invalid IP Entries
False Alerts and Log Pollution
Security tools may flag repeated entries of invalid IPs, leading to false positives and wasted investigative effort.
Spoofed or Bot Activity
Strings like this may emerge from automated bots or brute‑force tools testing address ranges, or as spoofed headers to evade detection.
Misconfiguration Impact
When invalid IPs like this enter firewall rules or DNS entries, they can lead to connectivity failures or security loopholes.
How IP Address Validation Works
Network tools typically validate addresses by checking that each octet falls in the 0–255 range and contains exactly four segments. Any deviation—like “2253”—is flagged as invalid. Popular tools such as Wireshark, WHOIS lookups, or Shodan simply ignore such entries.
What Real-World Incidents Teach Us
Organizations have reported anomalies where logs contained 185.63.2253.200, leading to deeper audits. In some cases, the string uncovered faulty login forms, while in others, malformed IoT firmware updates triggered error loops.
Tools to Investigate Suspicious IP Strings
Use tools like:
-
IP lookup platforms to test validity
-
Ping or traceroute commands to check connectivity
-
Regex or validation scripts to detect malformed patterns
Best Practices for IT and Cybersecurity Teams
-
Enforce input validation that rejects invalid octet values
-
Audit logs for recurring unusual IP patterns
-
Use anomaly detection rules in firewalls and SIEM systems to catch malformed addresses early
-
Block suspicious or malformed IPs where context demands
Volume of invalid entries should prompt review of automated scripts, bot activity, or misconfigured hosts.
Conclusion
While 185.63.2253.200 may appear structured like an IPv4 address, it fails technical validation and offers no real connectivity—yet its presence reveals much about formatting mistakes, bot behavior, and network hygiene. IT teams and aware users who understand why it’s invalid, know how to validate and respond, and implement secure logging practices will be better prepared in a world where even minor anomalies can point to deeper issues.